The following integration options are available to applications integrating with KEW:
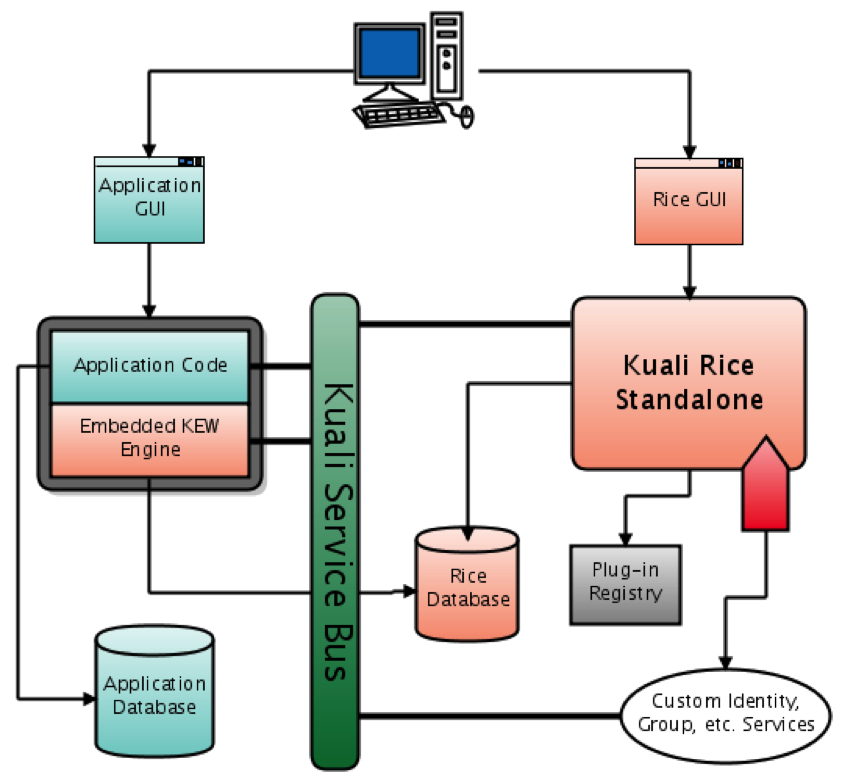
Embedded - The KEW engine is embedded into a Java application. The Standalone Rice Server is required.
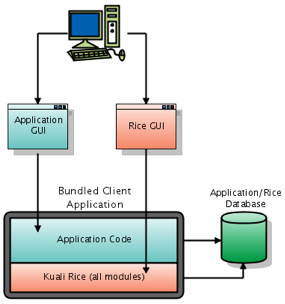
Bundled - Same as Embedded mode except that the entire KEW web application is also embedded into the Java application. The Standalone Rice Server is not required.
Remote Java Client – A Java client is used which relies on the service bus to communicate with a Standalone Rice Server’s KEW services.
Thin Java Client - A thin Java client is used which communicates with a Standalone Rice Server over remote service calls.
Web Services - Interacts directly with web services on a Standalone Rice Server.
Table 3.1. Advantages/Disadvantages of KEW Integration Options
| Integration Option | Advantages | Disadvantages |
|---|---|---|
| Embedded |
|
|
| Bundled |
|
|
| Remote Java Client |
|
|
| Thin Java Client |
|
|
| Web Services |
|
|
To effectively use any of the KEW integration modes besides bundled, a Standalone Rice Server will need to be deployed.
Bundled mode is the same as embedded mode except that the client application embeds the entire Kuali Rice system within it (including the web application). The embedding of the web application portion is accomplished by utilizing Struts Modules.
Configuration is the same as embedded mode, with the exception of loading the web application portions in the web.xml:
<filter>
<filter-name>UserLoginFilter</filter-name>
<filter-class>org.kuali.rice.kew.web.UserLoginFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>UserLoginFilter</filter-name>
<servlet-name>action</servlet-name>
</filter-mapping>
<servlet>
<servlet-name>action</servlet-name>
<servlet-class>org.apache.struts.action.ActionServlet</servlet-class>
.. other struts configuration if applicable
<init-param>
<param-name>config/en</param-name>
<param-value>/en/WEB-INF/struts-config.xml</param-value>
</init-param>
<load-on-startup>0</load-on-startup>
</servlet>
<servlet>
<servlet-name>remoting</servlet-name>
<servlet-class>org.kuali.rice.ksb.messaging.servlet.KSBDispatcherServlet</servlet-class>
<load-on-startup>1</load-on-startup>
</servlet>
<servlet>
<servlet-name>export</servlet-name>
<servlet-class>org.kuali.rice.kew.export.web.ExportServlet</servlet-class>
</servlet>
<servlet>
<servlet-name>attachment</servlet-name>
<servlet-class>org.kuali.rice.kew.notes.web.AttachmentServlet</servlet-class>
</servlet>
<servlet>
<servlet-name>edoclite</servlet-name>
<servlet-class>org.kuali.rice.kew.edl.EDLServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>remoting</servlet-name>
<url-pattern>/remoting/*</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>action</servlet-name>
<url-pattern>*.do</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>export</servlet-name>
<url-pattern>/export/*</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>attachment</servlet-name>
<url-pattern>/en/attachment/*</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>edoclite</servlet-name>
<url-pattern>/en/EDocLite</url-pattern>
</servlet-mapping>
org.kuali.rice.kew.web.UserLoginFilter – This filter is used to assist the KEW bundled web application in determining who the authenticated user is. Specifically, the login filter invokes the KIM identity management service to determine the identity of the authenticated user.
Typically, a previously executed filter will challenge the user on entry to a Rice web page for their authentication credentials using CAS or some other form of single sign on (SSO) authentication system.
For development and testing purposes, Rice provides a simple filter implementation that will present a simple sign on screen. This screen displays only a single login entry field and submit button. The user can enter their username (no password) and press the submit button, and the system authenticates the user for entry into the system.
This can be configured as follows in the web.xml:
<filter>
<filter-name>LoginFilter</filter-name>
<filter-class>org.kuali.rice.kew.web.UserLoginFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>LoginFilter</filter-name>
<servlet-name>action</servlet-name>
</filter-mapping>
and in the rice-config.xml:
<param name="filter.login.class">org.kuali.rice.kew.web.DummyLoginFilter</param> <param name="filtermapping.login.1">/*</param>
org.apache.struts.action.ActionServlet - The Struts servlet which loads the KEW Struts module. The module name should be 'en'. Struts only allows a single Action Servlet so if you are using Struts in your application, all of your Struts modules will need to be configured using the init-param elements in this servlet definition.
org.kuali.rice.ksb.messaging.servlet.KSBDispatcherServlet - A servlet which dispatches http requests for the Kuali Service Bus (see KSB documentation for more details). The servlet mapping here should correspond to the serviceServletUrl configuration parameter for the KSBConfigurer.
org.kuali.rice.kew.export.web.ExportServlet - serves exports of lookup results as XML files
org.kuali.rice.kew.notes.web.AttachmentServlet - serves attachments that have been attached to documents using the KEW Notes and Attachments framework
org.kuali.rice.kew.edl.EDLServlet - The servlet used to interact with eDocLite documents. See eDocLite documentation for more information.
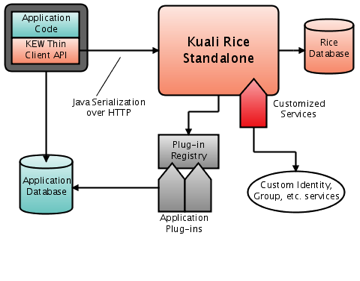
Along with the previous embedded configurations, KEW also allows for Remote Java Clients, which communicate with KEW services that are available on the service bus. Configuration of the remote client is similar to that of the embedded client, except that no embedded KEW engine gets set up; instead, the client relies on the service bus for accessing the KEW services of the Standalone Rice Server.
Caution
Limitations of Remote KEW Java Clients:
At present, KNS-enabled Java clients cannot be used as Remote KEW Java Clients.
In addition to the embedded configurations discussed previously, KEW also provides a thin java client which can be used to talk directly to two KEW services exposed on the service bus.
These KEW services are:
WorkflowDocumentService - provides methods for creating, loading, approving and querying documents
WorkflowUtilityService - provides methods for querying for various pieces of information about the KEW system
Additionally, access to two KIM services is required, as Principal and Group information is needed to use many of the methods in the KEW services above.
These KIM services are:
kimIdentityService - provides methods to query for Principal and Entity information
kimGroupService - provides methods to query for Group information
Of course, this configuration requires Standalone Rice Server deployment. The workflow engine deployed within Standalone Rice Server is used for processing documents that integrate using a thin client.
These services are exposed on the KSB as Java services, meaning they use Java Serialization over HTTP to communicate. Optionally, the KEW services can also be secured to provide access to only those callers with authorized digital signatures (note that secure access is required for the KIM services). In order to configure the thin client, the following configuration properties need to be defined.
Table 3.2. Required Thin Client Configuration Properties
| Property | Description |
|---|---|
| encryption.key | The secret key used by the encryption service; Must match the setting on the standalone server |
| keystore.alias | Alias of the application's key within the keystore |
| keystore.file | Path to the application's keystore file |
| keystore.password | Password to the keystore and the key with the configured alias |
| workflowdocument.javaservice.endpoint | Endpoint URL for the Workflow Document service |
| workflowutility.javaservice.endpoint | Endpoint URL for the Workflow Utility service |
| identity.javaservice.endpoint | Endpoint URL for the KIM identity service |
| group.javaservice.endpoint | Endpoint URL for the KIM group service |
Note
It is simplest to use an identical keystore file and configuration in your thin client application to that on your standalone server.
Table 3.3. Optional Thin Client Configuration Properties
| Property | Description |
|---|---|
| secure.workflowdocument.javaservice.endpoint | true/false value indicating if endpoint is secured (defaults to true); Must match the setting on the standalone server |
| secure.workflowutility.javaservice.endpoint | true/false value indicating if endpoint is secured (defaults to true); Must match the setting on the standalone server |
Here is the Spring configuration for a thin client in ThinClientSpring.xml:
<!DOCTYPE beans PUBLIC "-//SPRING//DTD BEAN//EN" "http://www.springframework.org/dtd/spring-beans.dtd">
<beans>
<!-- point Rice to the file containing your configuration params -->
<bean id="config" class="org.kuali.rice.core.config.spring.ConfigFactoryBean">
<property name="configLocations">
<list>
<value>classpath: yourThinClientApp-config.xml</value>
</list>
</property>
</bean>
<!-- Pull your configuration params out as Properties -->
<bean id="configProperties"
class="org.springframework.beans.factory.config.MethodInvokingFactoryBean">
<property name="targetObject" ref="config" />
<property name="targetMethod" value="getProperties" />
</bean>
<!-- expose configuration params to Spring -->
<bean class=
"org.springframework.beans.factory.config.PropertyPlaceholderConfigurer">
<property name="properties" ref="configProperties" />
</bean>
<!-- The RiceConfigurer that sets up thin client mode -->
<bean id="rice" class="org.kuali.rice.kew.config.ThinClientKEWConfigurer">
<!-- inject the "config" bean into our configurer -->
<property name="rootConfig" ref="config" />
</bean>
</beans>
Since KEW and KIM use the KSB to expose their services, the endpoint URLs are the same as those exported by the KSB.
An example configuration for these might be:
<param name= "workflowdocument.javaservice.endpoint">http://yourlocalip/kr-dev/remoting/WorkflowDocumentActionsService</param> <param name= "workflowutility.javaservice.endpoint">http://yourlocalip/kr-dev/remoting/WorkflowUtilityService</param> <param name= "identity.javaservice.endpoint">http://yourlocalip/kr-dev/remoting/kimIdentityService</param> <param name= "group.javaservice.endpoint">http://yourlocalip/kr-dev/remoting/kimGroupService</param>
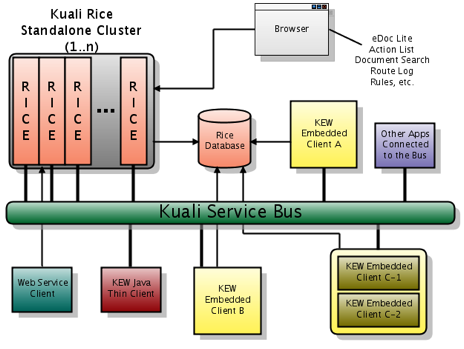
As can be seen from the various integration options described, a KEW Enterprise Deployment (and Kuali Rice in general) might very well be a distributed environment with multiple systems communicating with each other.
The diagram below shows what a typical Enterprise deployment of Kuali Rice might look like.
The display below includes those basic set of parameters for rice-config.xml as the minimal parameters to startup the Rice software. These parameters are a beginning reference to you for modification to your rice-config.xml.
Note
Please verify that your application.url and database username/password are set correctly.
Table 3.4. KEW Core Parameters
| Core | Description | Examples\Values |
|---|---|---|
| workflow.url | URL to the KEW web module (i.e., ${application.url}/en) | |
| plugin.dir | Directory from which plugins will be loaded | |
| attachment.dir.location | Directory where attachments will be stored |
As a minimum, you must enable the dummy login filter by adding these lines to the rice-config.xml file for default login screen:
<param name="filter.login.class">org.kuali.rice.kew.web.DummyLoginFilter</param> <param name="filtermapping.login.1">/*</param>
Table 3.5. KEW Configuration Properties
| Property | Description | Default |
|---|---|---|
| actionlist.outbox | Determines if the KEW actionlist "outbox" (ie, the actions already completed) will be viewable by users of the Rice application. | false |
| actionlist.outbox.default.preference.on | Determines if the KEW actionlist "outbox" is the default mode for viewing the action list. | false |
| base.url | Base URL under which Action List and other KEW screens can be found | Example: if your action list URL is http://yourlocalip/en/ActionList.do, set this property to http://yourlocalip/ |
| client.protocol | Same as clientProtocol property on KEWConfigurer, this property can be configured in either place | embedded |
| data.xml.root.location | The temporary location of files being processed by the KEW XmlPollingService | /tmp/${environment}/kew/xml |
| document.lock.timeout | Used by the Oracle database platform to determine how long database locks on the document header are used | |
| email.reminder.lifecycle.enabled | If true, turns on timed job to send out regular e-mails to remind users of actions still waiting in their action list | |
| extra.classes.dir | Directory where classes for KEW plugins are located | |
| extra.lib.dir | Directory where libraries for KEW plugins are located | |
| kew.mode | The mode that KEW will run in; choices are "local", "embedded", "remote", or "thin" | local |
| kew.url | The base URL of KEW services and pages | ${application.url}/kew |
| plugin.dir | Directory to load plugins from if the Plugin Registry is enabled | |
| plugin.registry.enabled | If set to true, then the Plugin Registry will be enabled and any available plugins will be loaded (see Workflow Plugin Guide) | false |
| attachment.dir.location | When using the attachments system, this is the directory where attachments will be stored | |
| data.xml.loaded.location | Directory path where the XML Loader will store successfully loaded XML files | |
| data.xml.pending.location | Directory path where the XML Loader will look for files to ingest | |
| data.xml.pollIntervalSecs | Interval in seconds that the XML Loader will poll the pending directory for new XML files to load | |
| data.xml.problem.location | Directory path where the XML Loader will put XML files it failed to load | |
| datasource.platform | The fully qualified class name of an implementation of the org.kuali.rice.core.database.platform.Platform interface | |
| default.note.class | The fully qualified class name of the default implementation of org.kuali.rice.kew.notes.CustomNoteAttribute to use for the Notes system | org.kuali.rice.kew.notes.CustomNoteAttributeImpl |
| edl.config.loc | Location to load the EDocLite component configuration from | classpath:META-INF/EDLConfig.xml |
| embedded.server | Indicates if an embedded instance is supposed to behave like a standalone server. See additional notes below under embedded.server | false |
| Identity.useRemoteServices | Configuration parameter that governs whether a number of common identity services (user and group service) are exported or retrieved via the bus. If this flag is set to true then:
| |
| initialDelaySecs | Delay in seconds after system starts up to begin the XML Loader polling | |
| rice.kew.enableKENNotification | Determines if KCB notifications should be sent for KEW events when Action Item events occur | true |
| rice.kew.struts.config.files | The struts-config.xml configuration file that the KEW portion of the Rice application will use | /kew/WEB-INF/struts-config.xml |
| workflow.documentsearch.base.url | The URL for the document search page | ${workflow.url}/DocumentSearch.do?docFormKey=88888888&returnLocation=${application.url}/portal.do&hideReturnLink=true |
| xml.pipeline.lifecycle.enabled | If set to true, will poll a directory for new Rice configuration XML and ingest any new XML placed in that directory | false |
If embedded.server parameter is enabled (set to true), then two additional features will be loaded when KEW is started:
XML Loader
Email Reminders
The XML Loader will poll a directory for XML files to ingest into the system (as configured by the data.xml.* properties).
The Email Reminders will handle sending Daily and Weekly batch emails for users that have their preferences set accordingly.
KEW requires and uses the database platform implementation in order to function. These may be be implemented differently for each support database management system.
The current functional implementations of this platform are:
org.kuali.rice.core.database.platform.OraclePlatform
org.kuali.rice.core.database.platform.Oracle9iPlatform (deprecated and just an alias for the OraclePlatform)
org.kuali.rice.core.database.platform.MySQLPlatform
When running a Standalone Rice Server, you may want to implement your own filters for authentication purposes. The system comes with a special filter that will read filter definitions and mappings from the configuration system.
The Bootstrap Filter is a generic filter that is applied to all web requests, which then delegates to any filters and are setup through the default configuration. This mechanism allows registration of institution-specific filters without the necessity of modifying the web application configuration file (/WEB-INF/web.xml) within the standalone webapp.
Filter syntax is as follows:
<param name="filter.filter name.class">class name of filter</param>
filter name is an arbitrary name for your filter:
<param name="filter.myfilter.class">edu.institution.organization.MyFilter</param>
Any number of configuration parameters may be defined for a given filter as follows:
<param name="filter.filter name.filter param name">filter param value</param>
For example:
<param name="filter.myfilter.color">red</param> <param name="filter.myfilter.shape">square</param>
For custom filters to be invoked, they must first be mapped to requests. That is done via the filter mapping parameter:
<param name="filtermapping.filter name.optional order index">path matching expression</param>
filter name is the name of your previously defined filter, optional order index is an optional integer used to specify the position of the filter in the invocation order, and path matching expression is a Servlet-specification-compatible url pattern.
<param name="filtermapping.myfilter.1">/special/path/</param>
If an order index is not specified, it is assumed to be 0. Filters with equivalent order are ordered arbitrarily with relation to each other (not in order of filter or mapping definition). A full example follows:
<param name="filter.myfilter.class">edu.institution.organization.MyFilter</param> <param name="filter.myfilter.color">red</param> <param name="filter.myfilter.shape">square</param> <param name="filter.securityfilter.class">edu.institution.organization.SecurityFilter</param> <param name="filter.securityfilter.secretKey">abracadabra</param> <param name="filter.compressionfilter.class">edu.institution.organization.CompressionFilter</param> <param name="filter.compressionfilter.compressLevel">5</param> <param name="filtermapping.securityfilter.1">/secure/</param> <param name="filtermapping.myfilter.2">/special/path/</param> <param name="filtermapping.compressionfilter.3">/*</param>
KEW can send emails to notify users about items in their Action List (depending on user preferences). Email in KEW uses the JavaMail library. In order to configure email, you will need to configure the appropriate JavaMail properties. A list of those properties can be found at the end of the page at the following url: http://java.sun.com/products/javamail/javadocs/javax/mail/package-summary.html
In addition to these standard JavaMail properties, you can also set the following optional properties to configure simple SMTP authentication.
Table 3.6. Optional Properties to Configure Simple SMTP Authentication
| Property | Description | Examples/Values |
|---|---|---|
| mail.transport.protocol | The protocol used to sending mail | smtp |
| mail.smtp.host | This is the host name of the SMTP | smtp.secureserver.net |
| mail.smtp.username | The username used for access to the SMTP server | |
| mail.smtp.password | The password used for access to the SMTP server |
Of course, if the authentication required by your mail server is beyond the abilities of the above configuration, it is possible to override the enEmailService loaded by the KEW module and implement a custom email service.
In order for KEW to send out emails, several steps need to be done. In order to have KEW send out any emails, the “SEND_EMAIL_NOTIFICATION_IND” KNS System Parameter needs to be set to ‘Y’. For emails to real people, the environment code must be set to ‘prd’. If this is not set to ‘prd’, an email can still be sent out to a test address. This test address is set by the KNS System Parameter, “EMAIL_NOTIFICATION_TEST_ADDRESS”. Emails sent in a test system will only be sent to the address specified by the EMAIL_NOTIFICATION_TEST_ADDRESS. The “from” address may also be set with a System Parameter. To do this, set the “FROM_ADDRESS” System Parameter to the email address you want the KEW emails sent from. If the FROM_ADDRESS parameter doesn’t exist or isn’t set, it will default to “admin@localhost”.
KEW can send emails on a nightly or weekly basis to remind users about items in their Action List (depending on user preferences). The following set of parameters configures whether the processes to send these reminders will run, and at what time(s) of day they will do so.
Table 3.7. Configuration Parameters for Email Reminders
| Property | Description | Examples/Values |
|---|---|---|
| email.reminder.lifecycle.enabled | Enable periodic KEW reminder emails | true |
| dailyEmail.active | Enable daily reminder emails | true |
| dailyEmail.cronExpression | Configures the schedule on which the daily reminder emails are sent – see org.quartz.CronExpression, org.quartz.CronTrigger for information about the format for this parameter | 0 0 1 * * ? |
| weeklyEmail.active | Enable weekly reminder emails | true |
| weeklyEmail.cronExpression | Configures the schedule on which the weekly reminder emails are sent – see org.quartz.CronExpression, org.quartz.CronTrigger for information about the format for this parameter | 0 0 2 ? * 2 |
Workflow users have the ability to update their preferences by going to the “User Preferences” page. The default values for many of these preferences can now be configured.
For example, institutions will commonly override the default action list email preference. By default it’s set to “immediate,” but it can be configured to “no”, “daily”, “weekly”, or “immediate.” The user will still be able to override the defaults on their User Preferences screen.
Here a list of workflow preferences that can be configured:
<!-- Default Option for Action List User Preferences. --> <param name="userOptions.default.color">white</param> <!-- email options: no, daily, weekly, immediate --> <param name="userOptions.default.email" >immediate</param> <param name="userOptions.default.notifyPrimary" >yes</param> <param name="userOptions.default.notifySecondary" >no</param> <param name="userOptions.default.openNewWindow" >yes</param> <param name="userOptions.default.actionListSize" >10</param> <param name="userOptions.default.refreshRate" >15</param> <param name="userOptions.default.showActionRequired" >yes</param> <param name="userOptions.default.showDateCreated" >yes</param> <param name="userOptions.default.showDocumentType" >yes</param> <param name="userOptions.default.showDocumentStatus" >yes</param> <param name="userOptions.default.showInitiator" >yes</param> <param name="userOptions.default.showDelegator" >yes</param> <param name="userOptions.default.showTitle" >yes</param> <param name="userOptions.default.showWorkgroupRequest" >yes</param> <param name="userOptions.default.showClearFYI" >yes</param> <param name="userOptions.default.showLastApprovedDate" >no</param> <param name="userOptions.default.showCurrentNode" >no</param> <param name="userOptions.default.useOutBox" >yes</param> <!-- delegatorFilterOnActionList: "Secondary Delegators on Action List Page" or "Secondary Delegators only on Filter Page" --> <param name="userOptions.default.delegatorFilterOnActionList" >Secondary Delegators on Action List Page</param> <param name="userOptions.default.primaryDelegatorFilterOnActionList" >Primary Delegates on Action List Page</param>
The Outbox is a standard feature on the Action List and is visible to the user in the UI by default. When the Outbox is turned on, users can access it from the Outbox hyperlink at the top of the Action List.
The Outbox is implemented by heavily leveraging existing Action List code. When an Action Item is deleted from the Action Item table as the result of a user action, the item is stored in the KEW_OUT_BOX_ITM_T table, using the org.kuali.rice.kew.actionitem.OutboxItemActionListExtension object. This object is an extension of the ActionItemActionListExtension. The separate object exists to provide a bean for OJB mapping.
The Workflow Preferences determine if the Outbox is visible and functioning for each user. The preference is called Use Outbox. In addition, you can configure the Outbox at the KEW level using the parameter tag:
<param name="actionlist.outbox">true</param>
When the Outbox is set to false, the preference for individual users to configure the Outbox is turned off. By default, the Outbox is set to true at the KEW level. You can turn the Outbox off (to hide it from users) by setting the property below to false:
<param name="actionlist.outbox.default.preference.on">false</param>
This provides backwards compatibility with applications that used earlier versions of KEW.
Notes on the Outbox:
Actions on saved documents are not displayed in the Outbox.
The Outbox responds to all saved Filters and Action List Preferences.
A unique instance of a document only exists in the Outbox. If a user has a document in the Outbox and that user takes action on the document, then the original instance of that document remains in the Outbox.
In addition to the previous discussion of KEW configuration, there are a few other aspects relevant to implementing KEW at your institution.
Because the operation of parts of KEW is dependent on a set of Document Types and Attributes being available within the system, there is some bootstrap XML that you will want to import. The easiest way to do this is to import the files in the following locations using the XML Ingester:
kns/src/main/config/xml/RiceSampleAppWorkflowBootstrap.xml
kew/src/main/config/bootstrap/edlstyle.xml
kew/src/main/config/bootstrap/widgets.xml
These files include the following:
Application constants: cluster-wide configuration settings
Core document types and rules: a few primordial document types and rules are required for the system to function
Default "eDocLite" styles: these are required if you wish to use eDocLite
Default admin user and workgroup: these are depended upon (at the moment) by the core document types and rules, as well as referred to by the default application constants
Application constants you may want to change:
Config.Application.AdminUserList: this should be set to a space-delimited set of administrative user names
Workflow.AdminWorkgroup: this should be set to an institutional admin workgroup; if the default KEW workgroup service is used, this can be left to the default, WorkflowAdmin
Config.Mailer.FromAddress: this should be changed to an address specific to your institution, e.g. kew@your-university.edu
HelpDeskActionList.helpDeskActionListName: set to an workgroup at your institution
ApplicationContext: set to the context path of the KEW application, if it differs from the environment default, e.g. "en-prod" instead of "en-prd"
In the core document types and rules config, you will need to change:
superUserWorkgroupName, blanketApproveWorkgroupName, and exceptionWorkgroup: should be set to the administrative group at your institution. If you are using the default workgroup service, this can be left as WorkgroupAdmin
ensure all docHandler elements, if they specify a URL, specify: "${base.url}/en-dev/Workgroup.do?methodToCall=docHandler", and ensure that the base.url config parameter is specified in your configuration (as mentioned above)